In the ever-evolving landscape of the digital world, the importance of security cannot be understated. As we usher in an era where data breaches, cyber-attacks, and identity thefts are commonplace, the need for strong and reliable methods to secure our data becomes paramount. Enter the realm of cryptographic algorithms – the unsung heroes working behind the scenes, ensuring the sanctity of our digital transactions and communications. Let’s embark on a journey to understand the basics of cryptographic algorithms and set the stage for our deep dive into the X11 Algorithm.
What is Cryptography?
At its core, cryptography is the art and science of encoding and decoding information to protect it from unauthorized access. Derived from the Greek words “kryptos” (hidden) and “graphia” (writing), its origins can be traced back thousands of years to ancient civilizations that used coded messages for secret communication during wars.
In the modern digital age, however, cryptography has transcended simple code writings. It now plays a crucial role in securing our digital lives, from ensuring safe online banking transactions to protecting sensitive personal data stored in cloud databases.
Types of Cryptographic Algorithms
Cryptography algorithms are broadly classified into two categories based on the type of keys used:
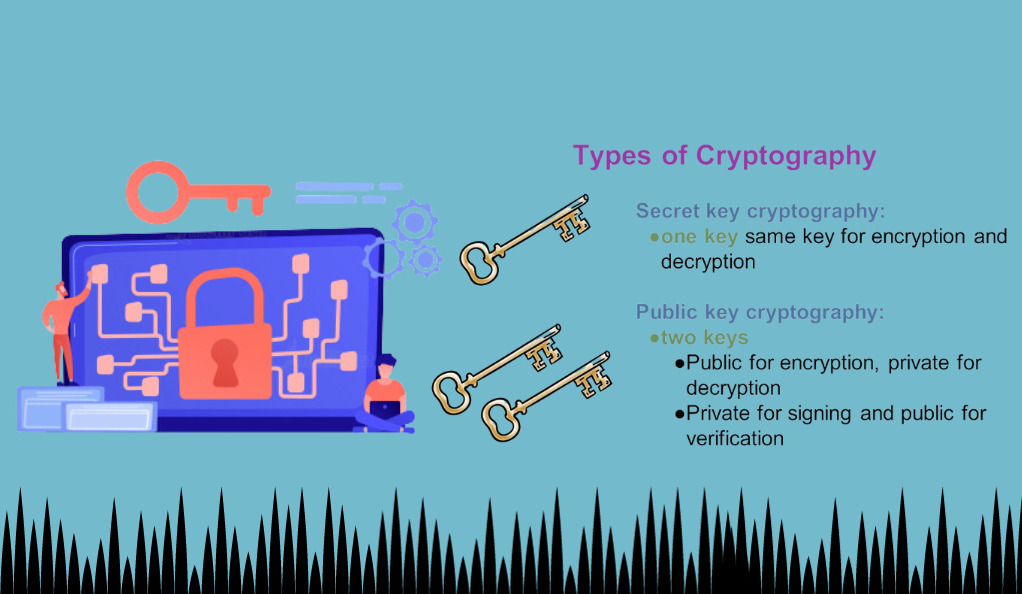
- Symmetric Key Algorithms (Private Key Cryptography):
- Key feature: Use the same key for both encryption and decryption.
- Examples: AES (Advanced Encryption Standard), DES (Data Encryption Standard), and Blowfish.
- Advantages: Faster and suitable for bulk data encryption.
- Drawbacks: Key distribution can be a challenge since both parties need access to the same key.
- Asymmetric Key Algorithms (Public Key Cryptography):
- Key feature: Use different keys for encryption and decryption – a public key for encryption and a private key for decryption.
- Examples: RSA (Rivest-Shamir-Adleman), DSA (Digital Signature Algorithm), and Elliptic Curve Cryptography.
- Advantages: Secure key distribution since the public key can be shared freely, while the private key remains confidential.
- Drawbacks: Slower due to the complexity of the algorithm, making it unsuitable for encrypting large amounts of data.
Setting the Stage for the X11 Algorithm
As you may already deduce, cryptographic algorithms are the bedrock of digital security. Whether it’s in securing online communications, authenticating users, or facilitating safe online transactions, they are omnipresent. One such cryptographic algorithm that has piqued interest, especially in the cryptocurrency domain, is the X11 Algorithm. Before we delve into its intricacies, it’s essential to understand its foundational place within the broader cryptographic landscape.
History of the X11 Algorithm
Cryptographic algorithms, much like any other technological innovation, are products of their time, sculpted by the challenges and needs they aim to address. X11, a notable member of this fraternity, boasts a rich history that adds context to its design philosophy and functionalities.
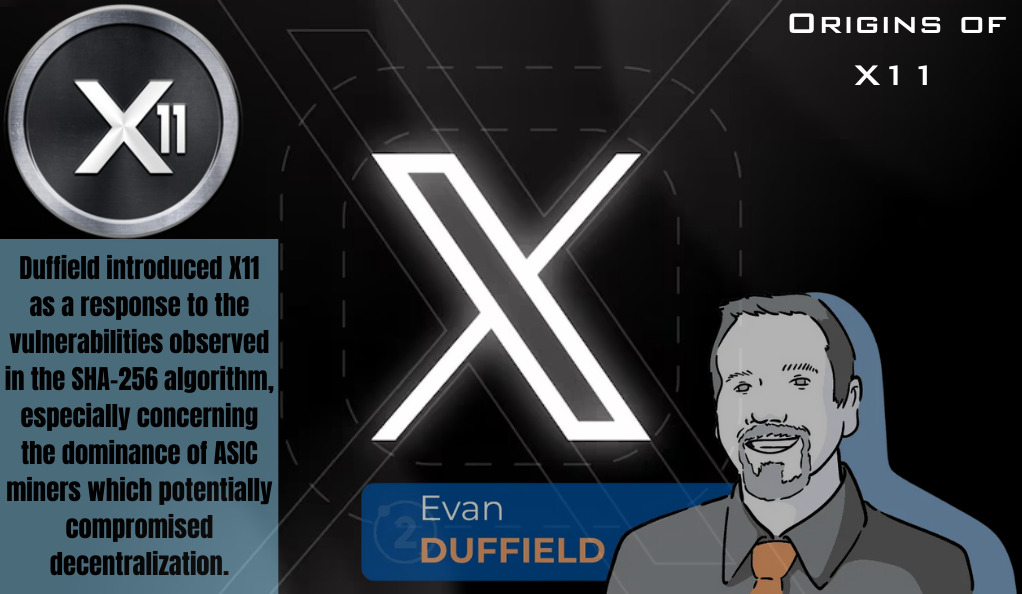
Origins of X11
X11 wasn’t conceived in isolation. It belongs to a family of algorithms known for their chained hashing techniques. Created by Evan Duffield, the inception of X11 can be tied to the launch of Dash (previously known as Darkcoin) in 2014. Duffield introduced X11 as a response to the vulnerabilities observed in the SHA-256 algorithm, especially concerning the dominance of ASIC miners which potentially compromised decentralization.
Duffield’s vision for X11 was clear: to craft a more intricate and multifaceted algorithm that would not only offer heightened security but also be resistant to ASIC mining, thereby promoting a more democratized mining landscape.
A Novel Approach: Chaining 11 Algorithms
What truly sets X11 apart is its chaining of eleven distinct cryptographic functions. This design decision wasn’t merely for complexity’s sake. By layering multiple algorithms, the security of the entire system is significantly bolstered. If a vulnerability is detected in one hashing function, the combined strength of the remaining ten serves as a formidable deterrent against potential threats.
Evolution Over the Years
X11’s journey hasn’t been static. Since its introduction, the algorithm has witnessed its share of tweaks, adjustments, and adaptations. It has paved the way for similar multi-hash algorithms like X13, X15, and X17, each adding more hashing functions to the mix.
Furthermore, as Dash gained prominence in the cryptocurrency market, the broader crypto community began to appreciate the nuances of X11, leading to its implementation in various other digital currency projects. While it remains most famously associated with Dash, the legacy of X11 transcends this association, serving as a testament to its robustness and adaptability.
A Balance of Security and Efficiency
The X11 Algorithm was not only designed to be secure but also energy efficient. The concerns about the high energy consumption of Bitcoin mining, primarily due to the SHA-256 algorithm, were growing. X11 addressed this by offering a cooler and quieter mining experience, reducing the overall energy footprint.
Why X11 Stands Out: 11 Hashing Functions
The heart of the X11 algorithm lies in its combination of eleven distinct cryptographic hashing functions. This amalgamation doesn’t just add complexity; it fundamentally enhances the security and resilience of the entire system. Let’s dive deeper into what these hashing functions are and the rationale behind integrating them into one comprehensive algorithm.
The Concept of Hashing
Hashing is the process of converting an input (often referred to as a “message”) into a fixed-length string of bytes. The output, known as the “hash value” or simply “hash,” appears random and is typically unique to each unique input. Changing even one bit of the input should ideally produce an entirely different hash, making it a critical component in verifying data integrity.
| Algorithm | Description |
|---|---|
| BLAKE | Known for high-speed performance on 64-bit platforms. |
| BMW (Blue Midnight Wish) | Recognized for strong security properties. |
| Groestl | Provides efficiency benefits, especially on platforms with AES support. |
| JH | A finalist in the NIST hash function competition. |
| Keccak | The foundation for the SHA-3 standard, offering a different approach compared to traditional hash functions. |
| Skein | Uses a tweakable block cipher and is known for its speed and security. |
| Luffa | Designed to be a versatile hash function with a wide range of output sizes. |
| Cubehash | A cryptographic primitive that’s quick in software operations. |
| SHAvite-3 | A fast, software-efficient function. |
| SIMD | Stands for ‘Single Instruction, Multiple Data’ – a parallel computing strategy. |
| ECHO | A hash function that operates on large data blocks, providing both security and efficiency. |
Layered Defense: The Power of Chaining
Using multiple hashing functions in tandem makes X11 remarkably secure. The idea is simple: even if a vulnerability arises in one hashing function, an attacker would still have to contend with the remaining ten. This structure offers a layered defense against potential threats.
Moreover, by leveraging the unique strengths of each hashing function, X11 ensures not only heightened security but also optimizes for efficiency and speed, particularly in the domain of cryptocurrency mining.
Addressing the ASIC Concern
The multi-hash approach of X11 also plays a pivotal role in its resistance to ASIC (Application-Specific Integrated Circuit) miners. ASICs, built specifically for mining purposes, overshadowed individual miners in networks governed by simpler algorithms like SHA-256. By elevating the complexity through multiple hashing functions, X11 levels the playing field, preserving the democratic ethos of cryptocurrency networks.
Benefits of Using the X11 Algorithm
X11, with its robust and multifaceted design, offers a plethora of benefits. These advantages make it a standout choice for developers, miners, and anyone vested in the domain of cryptographic algorithms. Let’s explore the salient features that have contributed to the increasing adoption and respect for the X11 Algorithm.
Enhanced Security Measures
- Layered Defense: As already discussed, the chaining of eleven different hashing functions significantly bolsters security. By spreading potential vulnerabilities across multiple algorithms, the risk is considerably mitigated. If one function is compromised, the combined strength of the remaining ten acts as a safeguard.
- Future-proofing Against Quantum Computing Threats: The diverse cryptographic methods employed by X11 provide some level of future-proofing. Concerns about quantum computers being able to break cryptographic algorithms are rising. The multi-hash structure of X11 might offer better resilience against such advancements.
Energy-Efficiency in Cryptocurrency Mining
X11 stands out in the world of cryptocurrency mining for its cooler mining operations and reduced energy consumption. This distinctive feature not only minimizes the heat generated by mining but also offers a more environmentally friendly option in an era when the environmental impact of mining is a significant concern.
Resistance to ASICs: A Boon for Miners?
- Democratizing the Mining Landscape: ASICs, being expensive and specialized pieces of hardware, led to centralization in cryptocurrency mining. X11, with its complex structure, proves to be a tough nut to crack for ASICs, bringing back the possibility of profitable mining operations for individual miners using standard hardware.
- Longer Hardware Lifespan: Due to reduced heat generation and energy consumption, hardware used to mine X11-based cryptocurrencies tend to have a longer lifespan. This is not only economical for miners but also reduces electronic waste.
Flexible and Adaptable Design
X11’s forward compatibility feature enables the replacement or modification of individual hashing functions, ensuring adaptability as cryptographic research advances. Additionally, cryptocurrencies like Dash, which employ the X11 algorithm, benefit from fast transaction speeds, making them suitable for everyday use and efficient financial transactions.
Challenges and Critiques of the X11 Algorithm
While the X11 Algorithm has garnered acclaim for its unique structure and the benefits it brings to the table, no technology is without its challenges and criticisms. It’s essential to view X11 from a balanced perspective, understanding both its strengths and areas of potential concern.
ASIC Development Challenges
Despite X11’s initial design to deter ASIC dominance, the technology landscape is ever-evolving. Over the years, ASIC developers have indeed created devices optimized for X11, thereby challenging the algorithm’s claim of ASIC resistance. This has reignited concerns about mining centralization for cryptocurrencies employing X11.
Complexity Can Be a Double-Edged Sword
- Increased Overhead: Layering eleven different cryptographic functions, while offering enhanced security, also introduces more points of potential failure. If a vulnerability or inefficiency arises, it can be more challenging to address given the intricate nature of the algorithm.
- Development Hurdles: For newcomers or those not intimately familiar with each of the eleven hashing functions, X11 can pose a steep learning curve. This can deter some developers from adopting or working with the algorithm.
Debates on Energy Efficiency
While X11 is indeed more energy-efficient compared to algorithms like SHA-256, it’s essential to place this in context. When compared to some newer algorithms designed explicitly for minimal power consumption, X11 may not always come out on top.
Adoption and Network Effects
- Beyond Dash: While Dash is the most notable cryptocurrency using X11, the algorithm hasn’t seen widespread adoption across the vast array of cryptocurrencies. This limited use can affect how much development attention and optimization X11 receives compared to more universally employed algorithms.
The Constant Evolution of Cryptography
In the ever-evolving landscape of cryptographic research and technology, X11, like any technology, must grapple with the constant challenge of remaining relevant and competitive.
Real-World Applications of the X11 Algorithm
The inception and development of the X11 Algorithm have not been in vain. Over the years, its application, primarily in the cryptocurrency domain, has provided tangible proof of its worth and capabilities. Delving into these real-world applications offers insights into the algorithm’s versatility and practicality.

Cryptocurrencies and X11
- Dash: The most notable cryptocurrency utilizing the X11 Algorithm. Dash, initially known as Darkcoin, was one of the pioneers in highlighting the benefits of this algorithm. With its InstantSend and PrivateSend features, Dash showcases the efficiency and transactional capabilities that X11 offers.
- CannabisCoin: A digital currency tailored for the legalized cannabis industry, CannabisCoin also adopted the X11 Algorithm. The decision was influenced by the algorithm’s energy-efficient mining operations and transactional speed.
- StartCoin: Designed to encourage crowdfunding campaigns, StartCoin opted for X11 to ensure quick, efficient transactions and an egalitarian mining environment.
X11 in Mining Pools
Given the algorithm’s inherent resistance to ASICs (at least in its early days) and its energy efficiency, numerous mining pools adopted X11. These pools allowed individual miners to combine their computational power to mine X11-based cryptocurrencies more effectively.
Security Applications
The chained hashing approach of X11 isn’t solely about cryptocurrency. Its intricate design can be used in various security applications, particularly in systems where data integrity and verification are paramount.
Digital Contracts and Verification Systems
The rapid and secure hashing capabilities of X11 make it suitable for digital contracts and other cryptographic verification systems. In scenarios where data needs to be irrevocably recorded and verified, the X11 Algorithm can serve as a foundational technology.
Future Potential: Beyond Cryptocurrencies
While X11 is primarily associated with digital currencies, its technical foundation has the potential for broader applications:
- Decentralized Applications (DApps): The efficient transaction processing and security capabilities of X11 can be harnessed in the growing world of DApps, particularly those requiring rapid data verification.
- Secure Data Storage: X11’s multi-layered hashing could be adapted for advanced secure data storage solutions, especially in sectors like healthcare or finance where data integrity is crucial.
The Evolution and Future Prospects of the X11 Algorithm
In the rapidly changing realm of cryptography and digital currencies, staying relevant and ahead of the curve is paramount. The X11 Algorithm, since its inception, has witnessed an evolution in its application and capabilities. Let’s chart this trajectory and envision what the future might hold for X11.
The Evolutionary Journey
- Initial Reception: When X11 was first introduced, it was lauded for its revolutionary approach. By incorporating eleven distinct hashing functions, it immediately set itself apart in terms of security and ASIC resistance.
- Adoption in the Crypto Sphere: Dash’s success shone a spotlight on X11, leading to its adoption by other cryptocurrencies. Mining pools specifically tailored for X11 began to emerge, indicating the growing interest and faith in the algorithm.
- ASICs Enter the Fray: Over time, the once ASIC-resistant nature of X11 began to wane as technology caught up. The introduction of X11 ASIC miners changed the landscape, raising questions about the algorithm’s long-term resilience against hardware-specific mining.
| Aspect | Description |
|---|---|
| Refinement & Adaptability | X11’s modularity allows for the replacement or tweaking of hashing functions, ensuring adaptability and relevance in the face of vulnerabilities or inefficiencies. |
| Beyond Cryptocurrencies | X11 has potential applications beyond digital currencies, particularly in tech sectors requiring robust data security and integrity solutions. |
| Research & Development | The dynamic world of cryptography necessitates continuous investment in research, allowing for the introduction of new algorithms or iterations inspired by X11’s core principles. |
| Community Engagement | Open dialogue and collaboration within the crypto and tech community can drive X11’s evolution by addressing critiques, incorporating feedback, and fostering a sense of communal ownership. |
Challenges and Roadblocks
While the future holds promise, it’s also fraught with challenges:
Staying Competitive: Newer algorithms, specifically tailored for minimal energy consumption or enhanced security, continually enter the market. X11 needs to prove its mettle against these newcomers.
Regulatory Hurdles: As governments and regulatory bodies worldwide grapple with the meteoric rise of digital currencies, algorithms like X11 might face scrutiny, especially if they become widely adopted.
Conclusion
The X11 Algorithm represents a remarkable achievement in cryptographic technology, seamlessly chaining eleven hashing functions to provide a unique blend of security, energy efficiency, and adaptability for digital currencies and beyond. Dash’s success as one of its prominent users demonstrates the algorithm’s capabilities, extending its promise to applications ranging from secure data storage to digital contract verification. While it faces challenges, such as ASIC development and competition from newer algorithms, X11’s modular design offers a roadmap for ongoing enhancement, ensuring its resilience and relevance.
In conclusion, the journey of the X11 Algorithm is a testament to innovation and adaptability in the ever-evolving digital landscape. It serves as a reminder of the constant interplay between technology and the challenges it addresses, shaping and being shaped by the world around it. Whether you’re a developer, a cryptocurrency enthusiast, or simply intrigued by cryptography’s intricacies, X11 undoubtedly holds a significant place in the realm of digital technology.
At axerunners.com, our goal is to furnish well-rounded and trustworthy information regarding cryptocurrency, finance, trading, and stocks. Nonetheless, we avoid providing financial advice and instead encourage users to conduct their own research and meticulous verification.
Read More













