In the rapidly evolving digital landscape, cryptocurrencies have emerged as revolutionary financial instruments, reshaping how we perceive and utilize money. As these digital assets gain traction, the importance of safeguarding them becomes paramount. This is where the realm of crypto forensics enters, a discipline dedicated to tracing, analyzing, and often recovering stolen or misplaced digital assets. One such asset that has garnered significant attention is the X11 cryptocurrency. This section delves into the significance of crypto forensics and introduces the reader to the world of X11 assets.
The Digital Gold Rush and Its Vulnerabilities
The 21st century has witnessed a digital gold rush, with cryptocurrencies at its forefront. Just as the gold rush of the 1800s attracted both genuine miners and malicious actors, the crypto boom has its share of cybercriminals. These individuals exploit vulnerabilities in digital wallets, exchanges, and sometimes the very blockchain that underpins these assets.
Why X11 Stands Out
X11, not to be confused with the X11 window system, is a unique cryptocurrency algorithm that uses a chain of eleven scientific hashing algorithms. This makes it one of the most secure encryption and hashing methods in the crypto world. Its multi-layered algorithmic structure ensures enhanced security, but it also becomes a prime target for cybercriminals due to its value and uniqueness.
The Need for Crypto Forensics
As the number of transactions, investments, and holdings in X11 and other cryptocurrencies increase, so does the potential risk of theft and fraud. Crypto forensics plays a pivotal role in mitigating these risks. By analyzing transaction patterns, tracing asset movements, and using advanced technological tools, crypto forensic experts can track down anomalies, trace stolen assets, and provide insights into potential security breaches.
Understanding X11 Cryptocurrency
The world of cryptocurrencies is vast and varied, with each digital asset bringing its unique features and technologies. Among these, X11 stands out not just for its name but for the robust security it offers.
What is X11 and Why is it Unique?
X11 is more than just another cryptocurrency; it represents a sophisticated algorithmic approach to digital asset security. Unlike many other cryptocurrencies that rely on a single hashing function, X11 employs a chain of eleven scientific hashing algorithms. This multi-algorithm structure ensures that even if one or a few of these algorithms were to be compromised, the entire system wouldn’t collapse. This redundancy provides an added layer of security, making it a favorite among security-conscious investors and users.
The Technology Behind X11
The strength of X11 lies in its chained hashing approach. The eleven algorithms that make up this chain are: BLAKE, BMW, Groestl, JH, Keccak, Skein, Luffa, Cubehash, Shavite, SIMD, and Echo. Each of these has its strengths, and when combined, they offer a formidable defense against potential threats.
By using multiple algorithms, X11 also ensures a fair distribution of mining power. In the world of crypto mining, the dominance of a single hashing function can lead to centralization, where a few powerful miners control the majority of the network. With X11’s approach, this risk is significantly reduced.
X11’s Environmental Edge
Another noteworthy aspect of X11 is its energy efficiency. Cryptocurrency mining is often criticized for its environmental impact due to the high energy consumption of mining rigs. X11’s design is such that it requires less power to mine, making it a more environmentally friendly option compared to some other cryptocurrencies.
| Algorithm | Primary Strength |
|---|---|
| BLAKE | High speed, security |
| BMW | Efficient compression |
| Groestl | Low power consumption |
| JH | Versatility, security |
| Keccak | Resistance to quantum attacks |
| Skein | Speed, security |
| Luffa | Parallelism |
| Cubehash | High diffusion, security |
| Shavite | Speed in hardware implementations |
| SIMD | Parallel processing |
| Echo | Resistance against differential attacks |
The Dark Side: Crypto Theft and X11
The allure of digital currencies, especially those as secure and unique as X11, inevitably attracts a spectrum of individuals, including those with malicious intent. As the value and adoption of X11 grow, so does the incentive for cybercriminals to exploit any potential vulnerabilities.
Common Methods Used by Cybercriminals
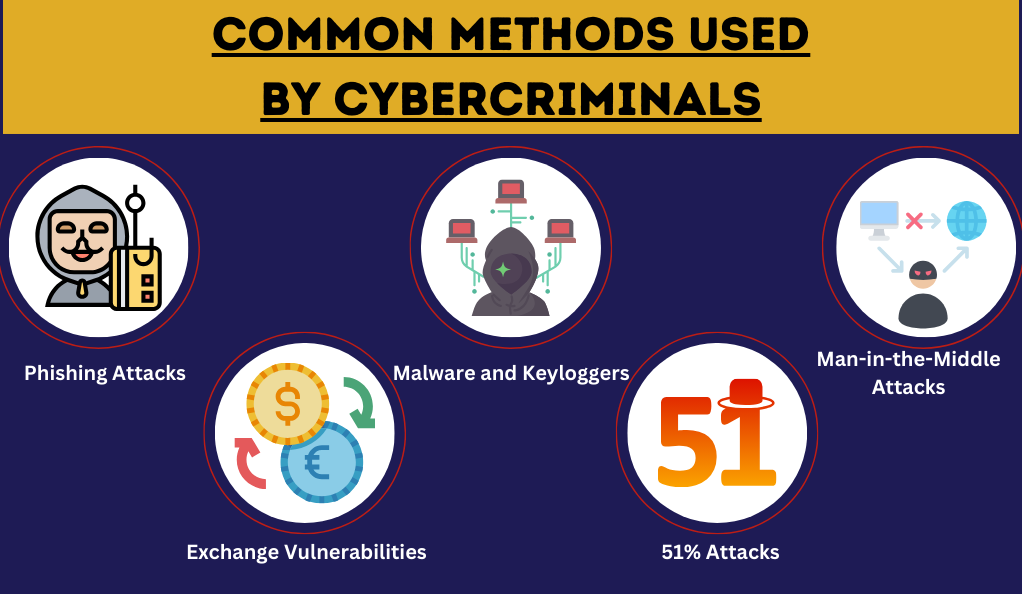
- Phishing Attacks: One of the most prevalent methods, phishing involves tricking individuals into revealing their private keys or login credentials. This is often done through fake websites or emails that mimic legitimate platforms.
- Malware and Keyloggers: Malicious software can be installed on a user’s device without their knowledge. These programs can record keystrokes, capturing passwords and other sensitive information.
- Man-in-the-Middle Attacks: Here, the attacker intercepts communication between two parties, altering or redirecting transactions without either party realizing until it’s too late.
- Exchange Vulnerabilities: Not all cryptocurrency exchanges are created equal. Some have weak security protocols, making them prime targets for hackers.
- 51% Attacks: Specific to the world of blockchain, this attack occurs when a single miner or mining pool controls over 50% of the network’s computational power, allowing them to double-spend coins.
Real-life Cases of X11 Asset Theft
While X11 is renowned for its security features, no system is entirely immune. There have been instances where X11 assets were compromised:
- The Exchange Breach: In a notorious case, an exchange that supported X11 was hacked, leading to a significant loss of assets. The breach was attributed to weak security protocols on the exchange’s part.
- The Wallet Scam: A fake X11 wallet app appeared on a popular app store, misleading users into transferring their assets to it. By the time the scam was identified, the perpetrators had vanished with a substantial sum.
- The Cloud Mining Trap: Investors were lured into a lucrative cloud mining scheme promising high returns on X11 mining. However, it turned out to be a Ponzi scheme, with new investments paying off the older ones until it inevitably collapsed.
| Attack Method | Primary Target | Prevention Measures |
|---|---|---|
| Phishing | Individual Users | Two-factor authentication, secure browsing |
| Malware/Keyloggers | Individual Devices | Regular software updates, antivirus software |
| Man-in-the-Middle | Transactional Data | Secure, encrypted connections |
| Exchange Vulnerabilities | Exchanges | Using reputable exchanges, cold storage |
| 51% Attacks | Blockchain Network | Decentralized mining, network monitoring |
Tracing Stolen X11 Assets
The digital nature of cryptocurrencies offers both challenges and opportunities when it comes to tracing stolen assets. Unlike traditional theft, where physical items are taken, in the crypto world, assets are transferred, often through a series of complex transactions designed to obfuscate the trail. However, the very technology that enables these transactions also provides tools for tracing them.
The Role of Blockchain in Tracking Asset Movement
Blockchain, the underlying technology of most cryptocurrencies, is essentially a public ledger. Every transaction made is recorded on this ledger, providing a transparent and immutable record. This transparency is a double-edged sword for cybercriminals. While they can see and potentially exploit transaction patterns, their illicit activities are also permanently etched onto the blockchain.
For X11 and similar assets, tracing a transaction means analyzing the blockchain to follow the movement of stolen assets from one address to another. While the addresses themselves are pseudonymous, patterns can emerge, especially when large sums are involved or when the assets move through known entities like exchanges.
Tools and Techniques Used in Crypto Forensics
Several tools and platforms have been developed to aid in crypto forensics:
- Blockchain Explorers: These are search engines for blockchains. They allow users to explore transactions, addresses, and blocks. For X11, specific explorers can track and display transactions in real-time.
- Cluster Analysis: By grouping together multiple addresses controlled by a single entity, cluster analysis can help identify patterns and potentially suspicious activities.
- Taint Analysis: This method traces the “taint” of stolen assets as they move through the blockchain, helping to identify which addresses have received stolen funds.
- Heuristic Analysis: By identifying patterns in how transactions are made, heuristic analysis can flag potentially suspicious activities or link multiple addresses to a single entity.
Challenges in Tracing Stolen Assets
While the tools and techniques are powerful, several challenges persist:
Mixers and Tumblers: These services are designed to obfuscate the trail of cryptocurrency transactions by mixing funds with others, making tracing significantly harder.
Cross-Chain Transactions: Moving assets between different blockchains can complicate the tracing process.
Jurisdictional Issues: Cryptocurrencies operate globally, and a transaction might involve entities from multiple countries, each with its regulations and levels of cooperation.
Forensic Tools vs. Challenges
Blockchain explorers are primarily used for tracking transactions, but their effectiveness is limited to specific blockchains. Cluster analysis helps group addresses together but can be thwarted by mixers that obfuscate the origin of funds. Taint analysis is used to trace stolen funds but has limited effectiveness when dealing with tumblers that mix transactions. Heuristic analysis, aimed at identifying patterns, requires extensive data for accuracy.
Recovering Stolen Assets: Is it Possible?
While tracing stolen X11 assets is a critical part of the crypto forensics process, the ultimate goal is often recovery. The burning question for victims of crypto theft is whether it’s possible to retrieve their assets once they’ve been stolen. The answer to this question is nuanced and depends on various factors.

Challenges in Asset Recovery
Asset recovery in the world of cryptocurrencies is not straightforward, primarily due to the pseudonymous nature of blockchain transactions. Here are some of the challenges:
Limited Identification: Addresses on the blockchain are pseudonymous, making it challenging to identify the real-world individuals or entities behind them.
Irreversible Transactions: Once a transaction is confirmed on the blockchain, it becomes nearly impossible to reverse it. Unlike traditional financial systems, there is no central authority to mediate disputes.
Cross-Border Complexity: Cryptocurrencies are borderless, which means that a stolen asset can quickly move across jurisdictions, making legal action complicated.
Success Stories and Lessons Learned
Despite these challenges, there have been instances where stolen X11 assets were successfully recovered, often through a combination of investigative work and legal action. Here are a few success stories:
- Collaboration with Exchanges: Some cryptocurrency exchanges have cooperated with law enforcement agencies to freeze or confiscate assets associated with criminal activities. This has been instrumental in recovering stolen funds.
- Blockchain Analysis: In cases where the stolen assets are moved through identifiable addresses or mixed with other assets, blockchain analysis can help track the movement and identify the perpetrators.
- Legal Recourse: Victims of crypto theft have sought legal action against hackers and thieves. In some cases, legal judgments have led to the return of stolen assets.
Prevention is Better than Cure
When it comes to safeguarding your X11 assets or any cryptocurrency, the age-old adage holds true: “Prevention is better than cure.” While it may not be possible to eliminate all risks, there are proactive steps that users and investors can take to minimize their exposure to theft and fraud.
Best Practices to Secure X11 Assets
- Use Hardware Wallets: Hardware wallets are physical devices that store your cryptocurrency offline, making them highly secure against online threats. They are considered one of the safest ways to store digital assets.
- Enable Two-Factor Authentication (2FA): Always enable 2FA on your cryptocurrency exchange accounts and wallets. This adds an extra layer of security by requiring a second authentication method in addition to your password.
- Regularly Update Software: Keep your wallets, software, and devices up to date. Software updates often include security patches that protect against known vulnerabilities.
- Beware of Phishing: Be cautious of unsolicited emails, messages, or websites that ask for your private keys or personal information. Double-check URLs to ensure they are legitimate.
- Cold Storage: Consider cold storage solutions, such as paper wallets or hardware wallets, for long-term storage of X11 assets. These are offline and, therefore, less susceptible to hacking.
- Diversify Storage: Don’t keep all your X11 assets in one place. Spread them across different wallets and exchanges to reduce the risk of losing everything in a single breach.
- Educate Yourself: Stay informed about the latest security threats and best practices in the cryptocurrency space. Knowledge is your best defense.
The Role of Crypto Wallets and Secure Exchanges
Crypto wallets and exchanges play a pivotal role in asset security:
Wallets: Choose reputable wallets with a track record of security. Research the wallet’s features, security measures, and user reviews before using it.
Exchanges: Use well-established and regulated exchanges. Look for exchanges that prioritize security, offer insurance for assets, and have a history of successfully handling security incidents.
The Future of Crypto Forensics
As the world of cryptocurrencies continues to evolve, so too does the field of crypto forensics. The relentless innovation in blockchain technology, coupled with the ever-growing complexity of cyber threats, paints an intriguing picture of what the future holds for the tracing and recovery of stolen X11 assets.
Emerging Technologies and Their Impact on Crypto Forensics
- AI and Machine Learning: Artificial intelligence and machine learning are becoming indispensable tools for crypto forensic experts. These technologies can analyze vast amounts of data, identify suspicious patterns, and help trace stolen assets more efficiently.
- Privacy Coins: The rise of privacy-centric cryptocurrencies presents new challenges for crypto forensics. Coins like Monero and Zcash make it extremely difficult to trace transactions, raising questions about the future of asset recovery.
- Blockchain Analytics Companies: Specialized companies are emerging that offer advanced blockchain analytics services. These firms provide forensic tools and expertise to track illicit activities on various blockchain networks.
- Global Regulations: As governments and regulatory bodies worldwide take a keener interest in cryptocurrencies, the legal landscape for crypto forensics is expected to evolve. New regulations may shape the way investigations are conducted and assets are recovered.
The Ongoing Battle Between Cybercriminals and Forensic Experts
The future of crypto forensics will undoubtedly be marked by an ongoing battle between cybercriminals and the experts who seek to thwart their activities. As criminals develop increasingly sophisticated techniques to hide their tracks, forensic experts will respond with innovative strategies and technologies.
Conclusion
In the constantly changing realm of cryptocurrencies, security remains a top concern. This article has delved into the world of crypto forensics, highlighting the challenges in tracking and recovering stolen X11 assets. While X11’s multi-algorithmic approach offers robust security, no system is immune to theft, and cybercriminals persistently innovate to exploit vulnerabilities. Successful asset recovery, driven by collaboration between exchanges, law enforcement, and forensic experts, offers hope to victims of theft.
Prevention is paramount for safeguarding X11 assets and cryptocurrencies in general. By adhering to best practices, diversifying storage, and staying informed, users can significantly reduce their exposure to theft and fraud. The future of crypto forensics is dynamic, shaped by emerging technologies, privacy coins, and global regulations. As the battle between cybercriminals and forensic experts rages on, users must remain vigilant to secure their digital wealth, recognizing that understanding asset security and crypto forensics is not merely prudent but essential in the digital age.
At axerunners.com, our goal is to furnish well-rounded and trustworthy information regarding cryptocurrency, finance, trading, and stocks. Nonetheless, we avoid providing financial advice and instead encourage users to conduct their own research and meticulous verification.
Read More










