In the rapidly evolving world of digital currencies, X11 Wallets have emerged as a popular choice for many crypto enthusiasts. These wallets, known for their robust encryption methods, promise a secure environment for digital transactions. However, as with all technological advancements, new challenges arise. One such challenge is the rise of quantum computing, a groundbreaking technology that has the potential to redefine the landscape of computational power and, consequently, the security protocols of digital wallets.
What are X11 Wallets?
X11 Wallets are digital wallets that utilize the X11 hashing algorithm, a chain of eleven different scientific hashing functions, to ensure the security of transactions. This multi-layered approach to encryption makes it considerably tough for potential hackers to breach, at least with the current computational capabilities.

Enter Quantum Computing
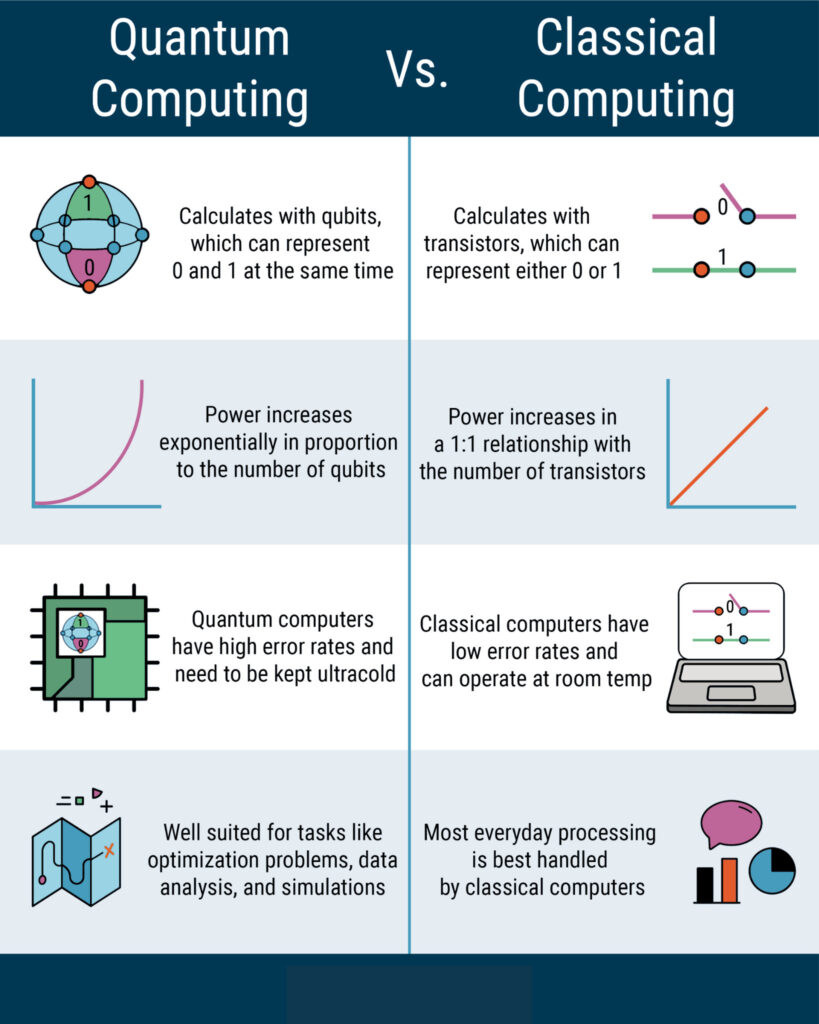
Quantum computing, on the other hand, operates on an entirely different level. Unlike classical computers that use bits (0s and 1s) to process information, quantum computers use quantum bits or qubits. These qubits can exist in a state of 0, 1, or both (known as superposition) simultaneously. This unique property allows quantum computers to perform multiple calculations at once, offering processing power that’s exponentially greater than that of classical computers.
The Impending Challenge
While the full potential of quantum computing is still being explored, its ability to solve complex problems in seconds that would take classical computers millennia is undeniable. This poses a significant threat to encryption methods, including those used by X11 Wallets. If a quantum computer can, in theory, decipher the X11 hashing algorithm, it could potentially expose countless digital transactions and the assets they protect.
| Comparison | Classical Computing | Quantum Computing |
|---|---|---|
| Basic Unit | Bit (0 or 1) | Qubit (0, 1, or both) |
| Processing Power | Limited | Exponentially High |
| Encryption Risk | Low | Potentially High |
What is Quantum Computing?
Quantum computing, often hailed as the next frontier in the world of computation, is a paradigm shift from the traditional binary systems we’ve grown accustomed to. But what exactly is it, and why is it causing ripples across various industries, especially in the realm of digital security?
The Quantum Realm
At its core, quantum computing draws inspiration from the principles of quantum mechanics, a fundamental theory in physics that describes the nature and behavior of matter and energy on the quantum (atomic and subatomic) scale. It’s a world where particles can exist in multiple states simultaneously and are intertwined through a phenomenon called entanglement.
Qubits: The Heart of Quantum Computing
Unlike classical computers that rely on bits, quantum computers use quantum bits, or qubits. A classical bit must be either 0 or 1, representing an electrical charge or its absence. A qubit, however, can represent a 0, a 1, or both 0 and 1 simultaneously, thanks to superposition. This ability to be in multiple states allows quantum computers to process a vast amount of information at once.
Harnessing Quantum Power
Imagine trying to solve a complex maze. A classical computer would attempt one route at a time, while a quantum computer could explore multiple routes simultaneously, drastically reducing the time needed to find a solution. This analogy underscores the potential of quantum computers to solve problems deemed unsolvable by classical means.
Implications for Cryptography
The very essence of cryptography lies in the complexity of certain mathematical problems. For instance, the security of many encryption schemes today relies on the difficulty of factoring large numbers into primes. While this is a hard task for classical computers, especially as the numbers grow larger, quantum computers could potentially make this task trivial with algorithms like Shor’s algorithm. This capability threatens the very foundation of cryptographic security, including the encryption methods used by X11 Wallets.
The Rise of Quantum Computing
The journey of quantum computing, from being a mere theoretical concept to a tangible technology, is nothing short of fascinating. As we trace its evolution, we’ll understand why it’s considered one of the most revolutionary advancements in the field of computation.
A Historical Perspective
The seeds of quantum computing were sown in the early 20th century when luminaries like Max Planck and Albert Einstein began to uncover the peculiarities of quantum mechanics. However, it wasn’t until the 1980s that the idea of a quantum computer was seriously considered. Richard Feynman and Yuri Manin were among the first to suggest that quantum mechanics could provide a new way to compute.
Milestones in Quantum Computing
- 1994: Peter Shor devises the Shor’s algorithm, which can factor large numbers exponentially faster than the best-known algorithms running on classical computers. This discovery raises alarms about the future security of cryptographic systems.
- 1996: Lov Grover introduces Grover’s algorithm, which can search an unsorted database faster than any classical algorithm, showcasing another potential advantage of quantum computing.
- 2000s: Companies and institutions worldwide begin investing heavily in quantum research, leading to the development of small-scale quantum processors and furthering the understanding of qubit behavior.
- 2019: Google claims “quantum supremacy” with its 53-qubit quantum computer named Sycamore. They report that it performed a specific task in 200 seconds, which would take the most advanced supercomputer thousands of years.
The Quantum Race
Today, tech giants like IBM, Google, and Microsoft, along with numerous startups, are in a race to build scalable and reliable quantum computers. Nations are also recognizing the strategic importance of quantum technology, leading to significant governmental investments in quantum research.
Potential vs. Reality
While the milestones achieved are impressive, it’s crucial to differentiate between the potential of quantum computing and its current reality. The quantum computers of today are still in their nascent stages, often termed “Noisy Intermediate-Scale Quantum” (NISQ) devices. They can perform specific tasks but are not yet ready to overthrow classical computers or break cryptographic systems universally.
The Quantum Threat to Encryption
As quantum computers become more advanced, the threat they pose to encryption methods, including the X11 hashing algorithm, becomes more pronounced. The ability to crack cryptographic codes, which secure everything from online banking transactions to private communications, is a looming concern. However, the crypto community is not standing still. Efforts are underway to develop quantum-resistant algorithms that can withstand the brute force of quantum machines.
X11 Wallets Explained
In the vast landscape of digital currencies, X11 Wallets have carved a niche for themselves, offering a unique blend of security and efficiency. But what sets them apart from the myriad of other digital wallets available? Let’s dive deep into the world of X11 Wallets.
The Genesis of X11
X11, as a term, refers to a chained hashing algorithm, which is a series of eleven different cryptographic functions. It was introduced with the launch of the Dash cryptocurrency (originally known as Darkcoin) in 2014. The primary motivation behind its creation was to offer better security and more efficient mining than its predecessors.
The Mechanics of X11
Unlike other hashing algorithms that rely on a single function, X11 employs eleven. These functions work in tandem, with the output of one serving as the input for the next. This chained approach makes it incredibly resistant to hacking attempts. Even if a potential vulnerability is found in one function, the subsequent ones act as additional layers of protection.
Benefits of X11 Wallets
- Enhanced Security: The multi-layered hashing approach makes it difficult for attackers to find vulnerabilities.
- Energy Efficiency: X11 is known for being more energy-efficient compared to other algorithms, making it a preferred choice for eco-conscious miners.
- Adaptive Mining: The design of X11 ensures that it remains resistant to custom hardware solutions or ASICs (Application-Specific Integrated Circuits), promoting a more decentralized mining landscape.

X11 in the Crypto Ecosystem
While Dash was the pioneer in using the X11 algorithm, several other cryptocurrencies have since adopted it, recognizing its benefits. This widespread adoption has further solidified the importance of X11 Wallets in the crypto ecosystem.
The Quantum Conundrum
Given the robustness of the X11 algorithm, one might assume that it’s impervious to threats. However, the rise of quantum computing challenges this notion. The sheer computational power of quantum machines could, in theory, decipher the X11 chain of algorithms, potentially compromising the security of assets stored in these wallets.
Potential Threats to X11 Wallets from Quantum Computing
The intersection of quantum computing and cryptography is a hotbed of research, debate, and anticipation. While X11 Wallets have been celebrated for their robustness, the looming shadow of quantum advancements raises pertinent questions about their future security.
The Quantum Advantage
At the heart of the concern is the unparalleled computational power of quantum computers. Their ability to process vast amounts of information simultaneously, thanks to the principles of superposition and entanglement, gives them a potential edge over classical systems. In the realm of cryptography, this advantage could be a game-changer.
Breaking the Chain
The X11 algorithm’s strength lies in its chained hashing approach. However, with quantum computers, there’s a potential to break this chain. Algorithms like Shor’s can, theoretically, factor large numbers exponentially faster than classical methods. If applied successfully, this could compromise the cryptographic foundation of X11 Wallets.
Real-World Implications
- Asset Vulnerability: If X11 encryption is breached, the assets stored within these wallets could be exposed, leading to potential theft or misuse.
- Loss of Trust: The crypto community relies heavily on the security of its encryption methods. A breach could erode trust, leading to decreased adoption and potential market instability.
- Regulatory Repercussions: Governments and regulatory bodies might enforce stricter regulations on digital currencies, further complicating the crypto landscape.
Defensive Measures and Future Innovations
As the quantum storm gathers on the horizon, the crypto community is not merely waiting to be swept away. Instead, it’s proactively seeking solutions, innovations, and strategies to ensure that the digital currency ecosystem remains secure and resilient in the face of quantum advancements.
Post-Quantum Cryptography
At the forefront of the defense strategy is post-quantum cryptography (PQC). This field of research focuses on developing cryptographic algorithms that are believed to be secure against the potential threats posed by quantum computers. While classical cryptographic systems rely on problems like integer factorization and discrete logarithms, PQC explores entirely different mathematical structures and problems.
Key Innovations in PQC
- Lattice-Based Cryptography: This approach relies on the complexity of certain problems in lattice structures, which, as of current understanding, are hard for quantum computers to solve.
- Hash-Based Cryptography: Instead of relying on traditional encryption methods, this system uses cryptographic hash functions to ensure security.
- Code-Based Cryptography: This method leverages the difficulty of decoding randomly generated linear codes, a problem that remains challenging even for quantum machines.
Transitioning to Quantum-Resistant Algorithms
While research into PQC is promising, transitioning from current cryptographic systems to quantum-resistant ones is not trivial. It requires:
- Standardization: Before widespread adoption, proposed quantum-resistant algorithms need to undergo rigorous scrutiny and standardization processes, ensuring they are both secure and practical.
- Integration: Existing systems, including X11 Wallets, need to be updated or replaced to integrate new algorithms, a process that demands time, resources, and careful planning.
- Education: The broader crypto community, from developers to end-users, needs to be educated about the changes, ensuring a smooth transition.
Collaborative Defense
Tech giants, startups, academic institutions, and governments are collaborating like never before. Initiatives like the National Institute of Standards and Technology’s (NIST) Post-Quantum Cryptography Standardization project are playing pivotal roles in driving the development and adoption of quantum-resistant cryptographic methods.
Conclusion
The evolution of technology is a tale of innovation, challenges, and adaptation. As we stand on the cusp of the quantum era, the crypto community finds itself at a pivotal juncture, balancing the promises of quantum computing with its potential threats to cryptographic systems like X11 Wallets. Embracing this change requires collective foresight, collaboration, and preparedness to ensure that the digital realm remains secure and resilient.
The relationship between X11 Wallets and quantum computing underscores the dynamic interplay between progress and security in the tech world. While challenges loom, the proactive stance of the global community offers hope. With unity and determination, we can navigate the complexities of the quantum age, turning potential threats into opportunities for growth and innovation.
At axerunners.com, our goal is to furnish well-rounded and trustworthy information regarding cryptocurrency, finance, trading, and stocks. Nonetheless, we avoid providing financial advice and instead encourage users to conduct their own research and meticulous verification.
Read More