Cryptocurrency, a revolutionary form of digital or virtual currency, has transformed the way we perceive and manage wealth. Just as traditional fiat currencies require physical wallets or bank accounts, cryptocurrencies need a special kind of ‘wallet’ for storage and management. But unlike the leather wallet in your pocket, a cryptocurrency wallet doesn’t “store” your money in the conventional sense. Instead, it provides a mechanism to access and manage your digital assets on their respective blockchains.
When venturing into the crypto landscape, one of the foremost decisions an investor has to make is the choice of a wallet. This decision can often determine the security and accessibility of their digital assets. Broadly, there are two primary types of crypto wallets: Hot and Cold. These terms might sound a bit abstract at first, but they essentially represent the connectivity of the wallet to the internet—and by extension, their vulnerability to online threats.

| Wallet Type | Connectivity | Typical Use | Security |
|---|---|---|---|
| Hot | Always online | Daily transactions, small amounts | Moderate to Low |
| Cold | Offline | Long-term storage, large amounts | High |
While both types have their own set of benefits and drawbacks, the fundamental distinction boils down to a trade-off between security and convenience. As we delve deeper into each type in the subsequent sections, we’ll explore their specific features, uses, benefits, and risks, equipping you with the knowledge to make an informed decision for your unique crypto needs.
What is a Hot Wallet?
Hot wallets are the go-to option for many newcomers to the cryptocurrency scene—and for good reason. At its core, a hot wallet is a digital cryptocurrency wallet that is continuously connected to the internet. This constant connectivity facilitates instant transactions, making it a popular choice for routine traders and casual crypto enthusiasts.

Definition and Characteristics
- Online Accessibility: Hot wallets are software-based and require an internet connection to operate. This can be in the form of a desktop application, a mobile app, or even a web interface.
- Private Key Storage: The private keys—cryptographic keys that allow you to access and manage your cryptocurrencies—are stored online or on a device connected to the internet.
- Third-party Services: Many hot wallets are provided by cryptocurrency exchanges or third-party services, enabling users to trade and manage their assets seamlessly on a single platform.
Typical Use Cases
- Daily Transactions: For users who transact frequently, hot wallets offer the convenience of rapid transfers. It’s akin to having cash in a physical wallet—easily accessible and ready to spend.
- Small Amounts: Given their online nature and the associated security risks (which we will delve into shortly), it’s advisable to store only small amounts of cryptocurrency in hot wallets, similar to the cash one might carry day-to-day rather than their life savings.
Advantages
- User-Friendly Interfaces: Hot wallets are designed with the average user in mind, boasting intuitive interfaces that make navigating the world of cryptocurrency a breeze—even for the uninitiated.
- Instantaneous Transactions: The online nature of hot wallets ensures that transactions can be conducted in real-time, perfect for those looking to capitalize on rapid market movements.
- Integrations with Exchanges: Many hot wallets are integrated with cryptocurrency exchanges, streamlining the process of buying, selling, and managing assets.
Risks Associated with Hot Wallets
Despite the undeniable convenience of hot wallets, their constant connection to the internet presents certain vulnerabilities. As with any online platform or service, hot wallets are susceptible to a variety of cyber threats.
Vulnerability to Online Attacks
- Phishing: This is a tactic where attackers masquerade as trustworthy entities to deceive individuals into providing sensitive information. A user might receive an email that appears to be from their wallet provider, urging them to click on a link and enter their private keys or passphrase. Once provided, the attacker can easily drain the wallet.
- Malware: If a user’s device is compromised by malicious software, the attacker might gain access to their wallet or even replace wallet addresses to redirect funds.
- Man-in-the-Middle Attacks: In this scenario, attackers intercept and potentially alter communications between two parties. This could mean altering the recipient address of a transaction without the user’s knowledge.
Dependency on Third-party Platforms
- Centralized Points of Failure: Wallets provided by exchanges or other third-party services centralize user funds, creating an enticing target for potential hackers.
- Downtime: Third-party platforms might experience outages, either due to technical glitches or overwhelming traffic. During such times, users might find themselves unable to access their funds.
Examples of Notable Breaches and Losses
- Mt. Gox: Once the world’s largest Bitcoin exchange, Mt. Gox declared bankruptcy in 2014 after hackers supposedly stole 850,000 Bitcoins. This incident stands as a grim reminder of the risks associated with centralizing vast amounts of cryptocurrency.
- Bitfinex: In 2016, this popular exchange suffered a breach that led to the theft of 120,000 Bitcoins. The platform had to temporarily shut down and later socialized the losses among its users.
Securing Hot Wallets
While the risks might seem daunting, users can adopt several strategies to bolster the security of their hot wallets:
- Two-Factor Authentication (2FA): This requires users to provide two distinct forms of identification before accessing their wallet, adding an extra layer of security.
- Regularly Updating Software: Keeping the wallet software updated ensures that users are protected from any known vulnerabilities.
- Beware of Phishing: Always double-check URLs and email senders. If something appears suspicious or too good to be true, it probably is.
- Using Strong, Unique Passwords: A robust password that isn’t reused across multiple platforms can deter potential unauthorized access.
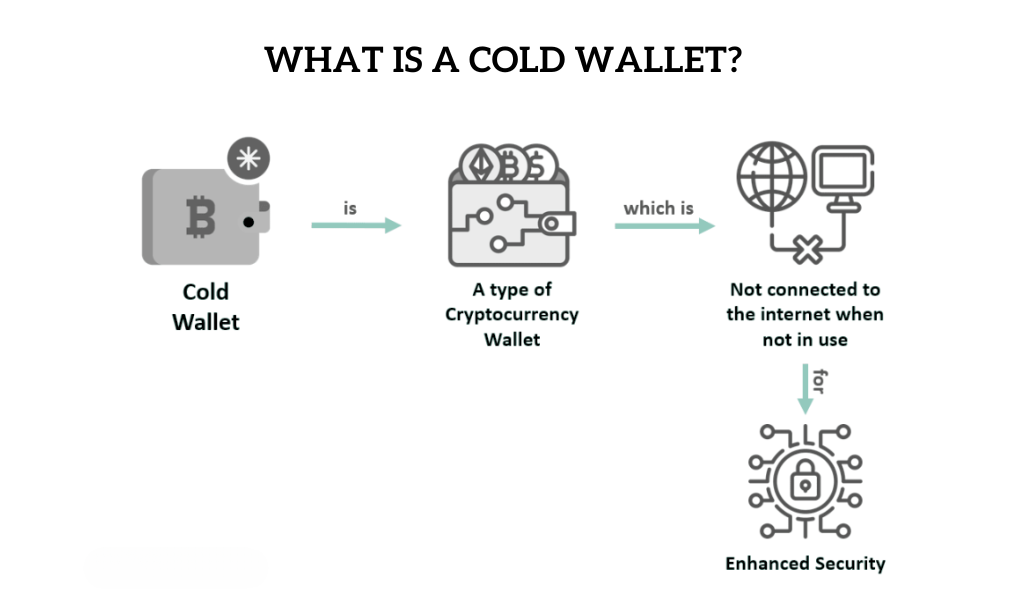
What is a Cold Wallet?
If you’ve ever stored precious items in a safety deposit box or bank vault, you already grasp the basic principle behind cold wallets. Essentially, cold wallets are cryptocurrency storage solutions that remain completely offline, insulated from the myriad of online threats that hot wallets might face. They are the fortified vaults of the crypto world, prioritizing security over quick access.
Definition and Characteristics
- Offline Storage: The defining feature of a cold wallet is its lack of connectivity to the internet. Whether it’s a hardware device or a paper wallet, it never communicates directly with the online world unless needed for a transaction.
- Private Key Protection: Cold wallets safeguard your private keys offline. Without these keys, your cryptocurrency remains inaccessible, which means they are safe from online hacking attempts.
- Physical Existence: Unlike hot wallets, which are primarily software-based, cold wallets often have a physical form, be it a hardware device or a printed piece of paper.
Typical Use Cases
- Long-term Storage: Cold wallets are ideal for “HODLers” – those who plan to hold onto their cryptocurrency for extended periods without frequent transactions.
- Large Amounts: Given their heightened security, cold wallets are the preferred choice for storing significant sums of cryptocurrency. It’s akin to storing gold in a vault rather than keeping it at home.
Advantages
- Enhanced Security: Without online connectivity, many of the vulnerabilities associated with hot wallets simply don’t apply to cold ones.
- Full Control: By not depending on third-party services, users maintain complete control over their crypto assets and private keys.
- Resistance to Online Hacks: Even if an attacker compromises a user’s computer or a crypto service platform, cold wallets remain unaffected, given they are offline.
Drawbacks of Cold Wallets
No solution is perfect, and while cold wallets offer exceptional security, they are not without their nuances. Before opting for a cold storage solution, it’s essential to be aware of its potential drawbacks to make an informed decision.
Accessibility Challenges
- Transaction Delays: Unlike hot wallets that allow for immediate transactions, accessing funds from a cold wallet requires connecting it to an online device or inputting details from a paper wallet. This additional step can introduce delays, making it less suitable for those requiring frequent, on-the-fly transactions.
- User Experience: Cold wallets, especially hardware variants, might have a steeper learning curve for the uninitiated. This can be intimidating for beginners in the crypto realm.
Risk of Physical Loss or Damage
- Hardware Failure: Just like any electronic device, hardware wallets can malfunction or get damaged. In such cases, recovering funds can be a complex task, though many devices do offer recovery options.
- Loss of Paper Wallets: If you’re using a paper wallet (a physical document containing your private and public keys), losing this piece of paper means losing access to your assets. There’s no “forgot my password” option in the world of crypto.
Initial Setup Complexity for Beginners
- Generating Wallets: While setting up a cold wallet, particularly a paper wallet, users must ensure they’re following secure procedures. This might involve offline computers, secure printers, and ensuring no potential exposure of the private key during the creation process.
- Safety Measures: Owners must take precautions against theft, fire, water damage, and other potential physical threats to their cold wallet.
Limited Functionality
Single-Purpose: Cold wallets are primarily designed for storage. They don’t offer the bells and whistles of hot wallet platforms, like integrated exchanges, market analysis tools, or staking opportunities.
Deciding Between Hot and Cold Wallets
The decision between hot and cold wallets isn’t always binary. Depending on individual needs, frequency of transactions, the value of assets, and personal risk tolerance, a hybrid approach might often be the most pragmatic choice.
Factors to Consider
- Amount of Crypto: If you’re dealing with small amounts meant for daily transactions, hot wallets provide the required convenience. However, for large holdings, the security of cold wallets is often recommended.
- Transaction Frequency: Active traders requiring rapid response to market fluctuations will find hot wallets more in line with their needs. In contrast, long-term investors might prioritize the safety of cold wallets.
- Security Concerns: How risk-averse are you? If the thought of potential online threats keeps you up at night, cold storage might offer better peace of mind.
- Technical Proficiency: Cold wallets, especially when setting up from scratch, can be technically demanding. If you’re not comfortable with these intricacies, using a reputable hot wallet or even a pre-configured hardware wallet might be more suitable.
Hybrid Approaches
For many, a blend of hot and cold storage offers the best of both worlds:
- Diversified Storage: Consider keeping a smaller, transactional amount in a hot wallet and the bulk of your assets in cold storage. This provides both ready access for daily needs and heightened security for long-term holdings.
- Regular Balancing: Depending on your trading activities and market gains, periodically review and shift assets between hot and cold storage to maintain an optimal balance.
- Utilize Hardware Wallets with Integrated Platforms: Some modern hardware wallets can seamlessly integrate with online platforms, offering a user-friendly interface while keeping the private keys offline and secure.
Conclusion
The digital realm of cryptocurrencies brings with it both unprecedented opportunities and challenges. Hot wallets, with their ease of use and quick accessibility, cater to those who value convenience and speed, while cold wallets stand as bastions of security, safeguarding assets against the myriad of online threats. However, neither solution is one-size-fits-all. It’s vital to weigh the unique benefits and trade-offs of each against individual needs, transaction frequency, and risk tolerance.
As the crypto landscape continuously evolves, staying informed and vigilant becomes paramount. Whether you’re an active trader or a long-term investor, your primary goal is the safety and accessibility of your digital assets. By understanding the intricacies of both hot and cold storage options and being proactive about security, you can navigate the complex waters of cryptocurrency with confidence and peace of mind.
At axerunners.com, our goal is to furnish well-rounded and trustworthy information regarding cryptocurrency, finance, trading, and stocks. Nonetheless, we avoid providing financial advice and instead encourage users to conduct their own research and meticulous verification.
Read More