In the ever-evolving world of digital currencies, the importance of robust security mechanisms cannot be overstated. As cryptocurrencies gain mainstream acceptance, the underlying technologies that support them, such as blockchain, become increasingly critical. One such technology that has garnered attention is the X11 wallet, a unique cryptographic solution designed for enhanced security. This article delves into the intricate relationship between blockchain technology and the security features of X11 wallets, shedding light on how they influence and enhance each other.
Blockchain: The Digital Ledger Revolution
Blockchain, often termed as the ‘digital ledger’, is a decentralized technology that records transactions across multiple computers in a way that ensures each transaction is secure, transparent, and immutable. Imagine a digital book, where each page of the book represents a ‘block’. Every time a transaction occurs, it’s recorded on a page. Once the page is full, it’s added to the book in a sequential manner. This book is viewable by anyone and is not stored in one place but rather copies of it are distributed across a network of computers, ensuring its security and transparency.
| Key Features of Blockchain | Description |
|---|---|
| Decentralization | No single entity has control, ensuring no single point of failure. |
| Transparency | All transactions are visible to anyone with access to the system, promoting trust among participants. |
| Immutability | Once a transaction is recorded, it cannot be altered, ensuring data integrity. |
| Security | Transactions are secured using cryptographic principles, making them tamper-proof. |
X11 Wallets: The Fortresses of Cryptocurrency
X11 wallets are digital tools that allow users to store, send, and receive cryptocurrencies. What sets X11 wallets apart is their unique cryptographic algorithm that uses a chain of 11 different hashing functions. This not only provides enhanced security but also makes them energy efficient, a concern with many cryptocurrencies.
The name ‘X11’ is derived from the 11 different cryptographic algorithms it employs, ensuring multiple layers of security. If one layer is compromised, the subsequent layers still protect the user’s assets. This multi-layered approach is what makes X11 wallets stand out in the crowded space of digital wallets.
Understanding Blockchain
Blockchain, at its core, is a revolutionary technology that promises to reshape numerous industries by offering transparency, security, and decentralization. To truly grasp its potential and its intersection with X11 wallet security, we must first delve into its foundational concepts and mechanisms.
The Essence of Blockchain
A blockchain resembles a digital ledger. However, instead of mimicking traditional ledgers, it spreads across a vast network of computers, or nodes. On this network, transactions group together in a ‘block’, which then joins a chronological ‘chain’ of prior transactions. The network continuously validates this chain of blocks, guaranteeing its authenticity and unchangeability.
Components of Blockchain:
- Block: A container data structure that encapsulates a list of transactions.
- Chain: A series of interconnected blocks that ensure a complete and unalterable history of transactions.
- Node: Individual computers on the blockchain network that validate and relay transactions.
- Consensus Mechanism: A technique used to achieve agreement on a single data value among distributed processes or systems.
Decentralization: The Heartbeat of Blockchain
Unlike centralized systems where a single entity holds authority, in a decentralized blockchain, authority is distributed. Every participant (or node) has access to the entire blockchain and complete transaction history. No single participant can alter past transactions without the consensus of the majority, making unauthorized actions virtually impossible.
Transparency and Immutability: Twin Pillars of Trust
One of the standout features of blockchain is its transparency. Every transaction is visible to anyone who wishes to see it, ensuring a transparent and trustless environment. Along with its unchangeable nature, which ensures that once added, no one can alter a transaction on the blockchain, it provides a level of security and trust that traditional systems can’t match.
Security Protocols: The Shield of Blockchain
Blockchain employs advanced cryptographic techniques to ensure the security of its transactions. Each block contains a unique code called a ‘hash’ and the hash of the previous block. This creates a chain where altering a single transaction would require changing the hash of every subsequent block, a feat nearly impossible given the decentralized validation mechanism of the network.
X11 Wallets Explained
In the vast ecosystem of cryptocurrency wallets, X11 wallets have emerged as a beacon of security and efficiency. But what exactly are X11 wallets, and how do they differentiate from the myriad of other wallets available? Let’s delve into the intricacies of X11 wallets and understand their significance in the crypto realm.
The Genesis of X11 Wallets
The term ‘X11’ might sound like a futuristic code, but in the world of cryptocurrencies, it represents a unique cryptographic algorithm. The ‘X11’ nomenclature is derived from its use of 11 different hashing functions, chained together to provide a multi-layered security protocol. This multi-algorithm approach not only bolsters security but also ensures energy efficiency, addressing one of the primary concerns associated with many cryptocurrencies.
| Hashing Functions in X11 | Purpose |
|---|---|
| BLAKE | Provides high speed and security. |
| BMW | Known for its efficient hardware implementation. |
| Groestl | Optimized for energy efficiency. |
| JH | Provides a high level of security and performance. |
| Keccak | The foundation for SHA-3, offering robust cryptographic strength. |
| Skein | Combines speed, security, and simplicity. |
| Luffa | Designed for parallel processing. |
| Cubehash | A high-speed hash function. |
| Shavite | Offers a balance between speed and security. |
| SIMD | Optimized for parallelism, enhancing processing speed. |
| Echo | Ensures cryptographic strength and efficiency. |
Features and Benefits of Using X11 Wallets
- Enhanced Security: The chain of 11 hashing functions guarantees protection. Even if attackers compromise one algorithm, the following layers actively defend the user’s assets, showcasing remarkable resilience against attacks.
- Energy Efficiency: Unlike Bitcoin’s energy-intensive Proof of Work (PoW), X11 uses a multi-algorithm approach designed for greater energy efficiency, showcasing its environmental friendliness.
- ASIC Resistance: X11’s design inherently resists the development of ASICs (Application-Specific Integrated Circuits) for mining, ensuring a more decentralized and equitable distribution of mining rewards.
- Faster Transaction Times: Thanks to its optimized algorithms, X11 wallets often boast quicker transaction confirmation times compared to other wallets.
- Future-Proofing: The X11 algorithm’s flexibility allows for the replacement of any hashing function found vulnerable in the future, guaranteeing the wallet’s sustained security and longevity.
Security Challenges in the Crypto World
The meteoric rise of cryptocurrencies has ushered in a new era of digital finance, offering unprecedented opportunities for global transactions, investments, and innovations. However, with these opportunities come significant security challenges. As the crypto ecosystem expands, so does the ingenuity of cybercriminals, making the security of digital assets a top priority. In this section, we’ll delve into the myriad of threats that loom in the crypto world and the role of blockchain in mitigating these challenges.
The Landscape of Crypto Threats
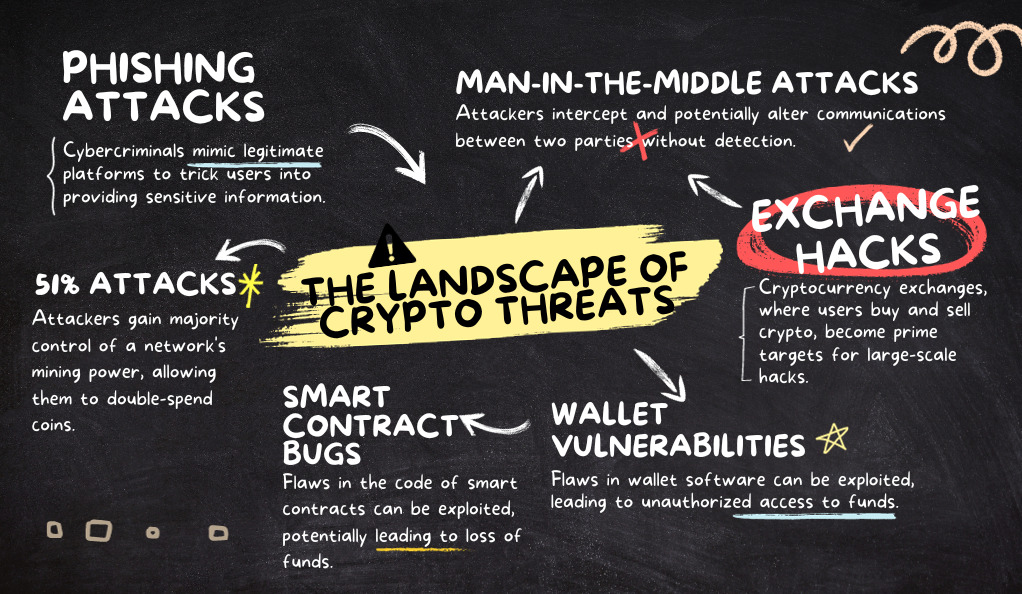
The decentralized nature of cryptocurrencies, while being one of their strongest features, also presents unique vulnerabilities. Here are some of the most prevalent security challenges faced by crypto users:
Threats in the Crypto World:
- Phishing Attacks: Cybercriminals mimic legitimate platforms to trick users into providing sensitive information.
- Man-in-the-Middle Attacks: Attackers intercept and potentially alter communications between two parties without detection.
- Exchange Hacks: Cryptocurrency exchanges, where users buy and sell crypto, become prime targets for large-scale hacks.
- Wallet Vulnerabilities: Flaws in wallet software can be exploited, leading to unauthorized access to funds.
- 51% Attacks: Attackers gain majority control of a network’s mining power, allowing them to double-spend coins.
- Smart Contract Bugs: Flaws in the code of smart contracts can be exploited, potentially leading to loss of funds.
Blockchain’s Role in Fortifying Security
Blockchain, with its foundational principles of decentralization, transparency, and immutability, acts as a bulwark against many of these threats:
- Decentralization: By distributing data across a vast network of nodes, blockchain eliminates single points of failure. This decentralized nature makes it incredibly challenging for attackers to compromise the system.
- Cryptography: Blockchain employs advanced cryptographic techniques, ensuring that each transaction is secure and tamper-proof. This makes unauthorized alterations virtually impossible.
- Transparency: Every transaction on the blockchain is visible to all participants. This transparency ensures that any malicious activity can be quickly detected and addressed.
- Consensus Mechanisms: The network must validate every transaction before adding it to the blockchain. This consensus mechanism guarantees the recording of only legitimate transactions.
- Regular Updates: Due to the open-source nature of many blockchain projects, a global community of developers actively reviews and improves them, quickly identifying and patching vulnerabilities.
How Blockchain Enhances X11 Wallet Security
The confluence of blockchain and X11 wallet security represents a significant stride in the safeguarding of digital assets. While both technologies individually offer robust security features, their intersection amplifies the protection manifold. In this section, we’ll explore the symbiotic relationship between blockchain and X11 wallets, highlighting how they complement each other to fortify the crypto ecosystem.
The Cryptographic Foundation of Blockchain
Blockchain’s security is deeply rooted in its adherence to cryptographic principles. Every transaction processed on the blockchain undergoes encryption through a distinct cryptographic signature, which vouches for its authenticity and permanence. Such encryption guarantees several things. Firstly, it ensures data integrity; after recording a transaction on the blockchain, any alteration would necessitate changes to all following blocks, a task that’s computationally daunting. Secondly, it provides robust authentication; only the genuine owner of the digital assets can initiate transactions, effectively barring unauthorized access. Lastly, even though the transactions themselves are transparent, the encryption masks the identities of the involved parties, preserving their privacy.
X11 Wallets and Blockchain: A Harmonious Partnership
X11 wallets, with their 11 hashing functions, offer multi-layered security. Combined with blockchain’s encryption, they provide unmatched protection. If attackers compromise one algorithm, the others, combined with blockchain’s defenses, actively protect users’ assets. Blockchain’s decentralized network validates transactions from X11 wallets, effectively deterring malicious activities. This collaboration ensures user privacy, with X11’s cryptography and blockchain’s encrypted identities preserving transaction confidentiality. Together, they create a secure, fair transaction environment resistant to ASIC mining.
Transaction Validation and the Role of Consensus Algorithms
One of the standout features of blockchain is its consensus algorithms, which ensure that all transactions are validated by the network before being recorded. When X11 wallets initiate transactions, they undergo this rigorous validation process:
- Proof of Work (PoW): This consensus mechanism requires network participants to solve complex mathematical problems, ensuring that transaction validation is computationally intensive and secure.
- Proof of Stake (PoS): This mechanism selects validators based on the number of coins they possess and their willingness to “stake” or set them aside as collateral. It offers a more energy-efficient alternative to PoW.
X11 wallets, with their energy-efficient design, are particularly well-suited for PoS consensus mechanisms, ensuring faster and more environmentally friendly transaction validations.
Potential Risks and Limitations
While blockchain technology and X11 wallets offer a formidable defense against many security threats, it’s essential to recognize that no system is entirely invulnerable. As with any technology, there are potential risks and limitations that users should be aware of. This section aims to shed light on these challenges, ensuring that users are well-informed and can navigate the crypto landscape safely.
Understanding the 51% Attack
One of the most discussed vulnerabilities in the blockchain world is the 51% attack. This attack occurs when a single entity or group gains control of more than half of the network’s mining power.
Understanding the 51% Attack:
- How it works: If an attacker gains majority control, they can exclude or modify the ordering of transactions. This capability enables them to double-spend coins, meaning they can use the same coins for multiple transactions.
- Impact: An attack of this nature can erode trust in a blockchain, potentially causing a decline in the value of the associated cryptocurrency.
- Mitigation: To counteract the risk of a 51% attack, solutions include the implementation of varied consensus mechanisms, consistent network monitoring, and promoting decentralized mining practices.
The Debate Between Public and Private Blockchains
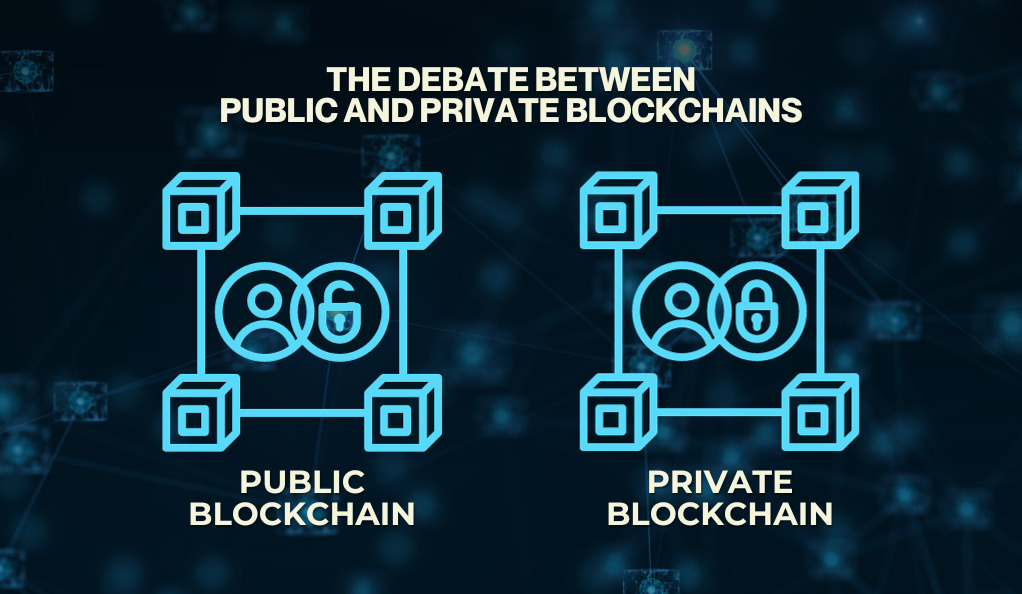
Blockchain technology splits into two main categories: public (or permissionless) and private (or permissioned) blockchains. Public blockchains welcome everyone and stand out for their strong decentralization, transparency, and immutability. However, they come with challenges such as slower transaction speeds, greater energy consumption, and potential scalability concerns. On the other hand, private blockchains offer faster transaction speeds and efficiency. They can also be tailored to suit specific industry needs. But they come with their own set of limitations, including reduced decentralization. Users must also place trust in the governing entity, and there might be limitations on transparency. When considering X11 wallets, the choice of blockchain type hinges on the specific use-case. It’s a decision that weighs transparency against speed and control, ensuring the best fit for the user’s needs.
Smart Contract Vulnerabilities
Smart contracts, self-executing contracts with the terms directly written into code, are a significant feature of many blockchains. However, they’re not without their challenges:
- Immutable but not Immune: Once developers deploy smart contracts, they remain unalterable. However, any bugs in the code present an exploitable vulnerability unless they implement preventive measures.
- Complexity Risks: The more complex a smart contract, the higher the risk of unforeseen vulnerabilities.
- Gas Limitations: On platforms like Ethereum, smart contracts consume ‘gas’. If a contract requires more gas than currently available, it can stall.
Future-Proofing Challenges
The rapid evolution of technology means that what’s secure today might be vulnerable tomorrow. Both blockchain and X11 wallets need continuous updates and adaptations to stay ahead of potential threats.
Future Prospects and Developments
The world of digital currencies is in a constant state of flux, with innovations and advancements emerging at a breakneck pace. Both blockchain technology and X11 wallets are at the forefront of this evolution, continuously adapting and evolving to meet new challenges and harness fresh opportunities. In this section, we’ll cast a gaze into the future, exploring the potential trajectories of these technologies and their implications for the broader crypto ecosystem.
The Evolving Landscape of Blockchain Technology
Blockchain, since its inception, has grown beyond just being the backbone of cryptocurrencies. Its potential applications are vast and varied:
- Decentralized Finance (DeFi): Blockchain is revolutionizing the financial sector, enabling peer-to-peer financial systems without intermediaries.
- Supply Chain Management: Ensuring transparency and traceability in product sourcing and delivery.
- Healthcare: Securely storing and sharing patient data, improving diagnosis and treatment.
- Voting Systems: Creating tamper-proof and transparent voting mechanisms for elections.
With these advancements, the security and efficiency of blockchain will be under increased scrutiny, necessitating further innovations.
How X11 Wallets are Adapting to New Security Challenges
As cyber threats become more sophisticated, X11 wallets are not resting on their laurels:
- Multi-Signature Protocols: Systems now require multiple signatures to authorize a transaction, thereby enhancing security.
- Biometric Security: Integrating fingerprint and facial recognition to ensure that only the rightful owner can access the wallet.
- Cold Storage Solutions: Offering offline storage options to protect assets from online vulnerabilities.
- Interoperability: Ensuring that X11 wallets can seamlessly operate across different blockchains, enhancing user experience and flexibility.
The Role of Quantum Computing
One of the most significant potential disruptors for both blockchain and X11 wallets is the advent of quantum computing. Quantum computers, with their ability to perform complex calculations at unprecedented speeds, pose a potential threat to cryptographic systems:
Implications of Quantum Computing on Cryptography:
- Cryptographic Algorithms: Quantum computers have the potential to break specific cryptographic algorithms. This challenge emphasizes the importance of developing quantum-resistant algorithms.
- Transaction Speeds: While quantum computing can significantly accelerate transaction validations, it might introduce scalability challenges that need addressing.
Both blockchain and X11 wallet developers are keenly aware of these implications and are actively researching quantum-resistant solutions.
Sustainability Concerns
The environmental impact of certain blockchain networks, especially those relying on energy-intensive consensus mechanisms like Proof of Work (PoW), has come under scrutiny. Future developments will likely focus on more energy-efficient consensus mechanisms, and X11’s inherent energy efficiency will play a pivotal role in this transition.
Conclusion
As we conclude our exploration into the dynamic interplay between blockchain and X11 wallet security, it’s evident that their convergence offers a robust shield for digital assets in the ever-evolving crypto landscape. Blockchain, with its foundational principles of decentralization, transparency, and immutability, synergizes perfectly with the multi-layered cryptographic approach of X11 wallets, promising users a secure and efficient digital experience.
However, the onus of security doesn’t solely lie on technology. For individuals navigating the crypto world, staying informed, adopting best practices, and using trusted platforms are paramount. As we look to the future, the combined strengths of blockchain and X11 wallets serve as a beacon, guiding us towards a more secure and transparent digital realm.
At axerunners.com, our goal is to furnish well-rounded and trustworthy information regarding cryptocurrency, finance, trading, and stocks. Nonetheless, we avoid providing financial advice and instead encourage users to conduct their own research and meticulous verification.
Read More